记录一些CTF中常用的密码学工具用法
crypt-commons
https://github.com/p4-team/crypto-commons
yafu
因式分解工具,支持Windows与Linux,可以在sourceforge下载,用法也很简单:
1 | ➜ ~ ./yafu |
RSA tools
用来进行RSA计算的,提供pq或者nd产生私钥,安装:
1 | git clone https://github.com/ius/rsatool.git |
使用:
1 | python rsatool.py -f PEM -o key.pem -n 13826123222358393307 -d 9793706120266356337 |
openssl
实在太强大,这里就记录一下最简单的用法:
1 | openssl genrsa -out private.pem 1024 |
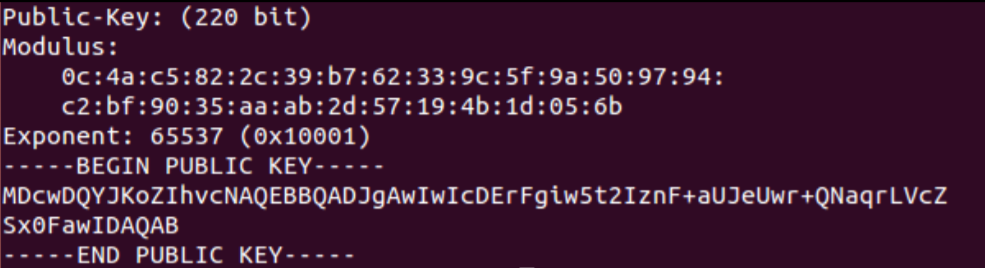
这种东东的破解,就是提取出中间的16进制用yafu分解
RsaCtfTool
1 | git clone https://github.com/Ganapati/RsaCtfTool |
一个很强大的专肝ctf的rsa密文恢复工具,支持如下攻击技术:
Weak public key factorization
Wiener's attack
Hastad's attack (Small public exponent attack)
Small q (q < 100,000)
Common factor between ciphertext and modulus attack
Fermat's factorisation for close p and q
Gimmicky Primes method
Past CTF Primes method
Self-Initializing Quadratic Sieve (SIQS) using Yafu
Common factor attacks across multiple keys
Small fractions method when p/q is close to a small fraction
Boneh Durfee Method when the private exponent d is too small compared to the modulus (i.e d < n^0.292)
Elliptic Curve Method它的用法也很简单,直接看手册就好了,GitHub上也有一些例子可以直接拿来用
hashpump
用来进行hash长度扩展攻击的,可以编译安装C版:
1 | git clone https://github.com/bwall/HashPump.git |
也可以安装python版
1 | pip install hashpumpy |
接着使用
1 | import hashpumpy |
python-paddingoracle
进行paddingoracle攻击的工具,安装
1 | git clone https://github.com/mwielgoszewski/python-paddingoracle.git |
xortool
使用频率分析猜测异或秘钥再解出明文,当然也支持xor加密操作,安装:
1 | pip install xortool |